Chapter 1: Introduction—Strategic Positioning and Core Essence of National-Level Cyberspace Security Attack-Defense Exercises
1.1. Concept Definition and Evolution
National-Level Cyberspace Security Attack-Defense Exercises (hereafter referred to as "exercises") are strategic, systematic activities planned and organized at the highest national level. By simulating real-world cyberattacks and defensive confrontations in a highly realistic network environment, they aim to comprehensively test, evaluate, and enhance a nation's overall cyberspace security capabilities and readiness. In essence, they are "digital rehearsals" for cyber warfare and "extreme stress tests" for national cyber resilience.
The concept of these exercises has evolved profoundly. Initially, they were more focused on technical-level penetration testing and vulnerability verification, aiming to discover and patch system weaknesses. As cyberspace was officially established as the "fifth domain of warfare" after land, sea, air, and space, the scope of these exercises has expanded to a comprehensive national strategic action, encompassing strategic deterrence, readiness inspection, capability generation, talent cultivation, and ecosystem construction.

Figure Caption 1.1: The command center of a national-level attack-defense exercise serves as the brain of the cyberspace "digital battlefield." Using advanced visualization technology, it aggregates global cyber threat intelligence, real-time attack-defense confrontations, and the status of critical infrastructure onto a single screen, providing strategic decision support for commanders. This visually represents the exercise's strategic height and complexity as a "digital rehearsal" for cyber warfare.
Core Features:
- High Fidelity: Utilizes technologies like cyber ranges and digital twins to construct network topologies, business systems, data traffic, and electromagnetic environments that are highly similar to the real world, simulating realistic attacker Tactics, Techniques, and Procedures (TTPs).
- Strong Adversarial Nature: Attacking (Red Team) and defending (Blue Team) sides engage in real-time, continuous technical and tactical games under "back-to-back," asymmetric information conditions, with extremely high intensity and complexity.
- All-Element Scope: Involves not only the confrontation of technical tools but also a comprehensive test of all security elements, including organization, management, processes, personnel, and collaboration, constituting a full-scale assessment of the entire defense system.
- Real-Combat Orientation: The objectives, scenarios, and assumptions of the exercises are directly derived from real-world cyber threat intelligence, major security incidents, and geopolitical conflicts. The results directly serve to enhance practical capabilities for responding to real cyber warfare.
Similarities and Differences with Real Cyber Warfare: Exercises are the highest form of cyber warfare simulation under "laboratory" conditions. The two share a high degree of consistency in target selection, attack paths, and technical means. However, the fundamental difference lies in that exercises are always conducted within a controllable legal and ethical framework. Their destructive consequences are strictly limited, and political impacts are carefully managed, avoiding the irreversibility and unlimited escalation risks of real war.
| Dimension | National-Level Attack-Defense Exercise | Real Cyber Warfare |
|---|---|---|
| Objective | Test capabilities, identify weaknesses, cultivate talent, improve systems | Achieve political/military goals, paralyze the enemy, acquire intelligence |
| Risk Control | Risks are controllable, processes are reversible, with clear termination rules | Risks are extremely high, consequences are irreversible, prone to conflict escalation |
| Legal Boundary | Conducted within an authorized legal framework (adhering to Rules of Engagement, RoE) | Vague or disregards international law, seeks "extra-legal" advantage |
| Political Impact | Controlled release of strategic signals, combining deterrence and communication | Direct state-level confrontation, may trigger all-out war |
| Scope | Pre-defined scope, focusing on specific critical infrastructure or domains | All-domain, unrestricted, may affect the global network |
1.2. The Cornerstone of National Security: Strategic Significance in the New Era
Against the backdrop of deep integration between the digital and physical economies and the extension of great power competition into cyberspace, the strategic value of national-level attack-defense exercises has reached an unprecedented height.
- A Core Measure to Defend Cyberspace Sovereignty: Cyberspace sovereignty is a natural extension of national sovereignty into the network domain. By simulating attacks from external forces on our nation's network infrastructure, exercises test the country's autonomy, control, and survivability under extreme conditions. They are a practical action to declare and defend our cyberspace sovereignty, ensuring the nation's digital lifeline remains firmly in our own hands.
- A "Stress Test" to Secure Critical Information Infrastructure (CII): Critical sectors like power, finance, transportation, communications, and energy are the nation's "nervous system" and primary targets for cyberattacks. Exercises are currently the only known method capable of simulating high-intensity, persistent, and systematic attacks against CII. They can most effectively expose deep-seated, systemic risks in technology, management, and operations, serving as the ultimate "touchstone" for ensuring CII security and resilience.
- A "Whetstone" for Enhancing National Overall Cyber Defense Capabilities: Modern cyber defense can no longer be achieved through "single-point defense." It requires building a systematic defense capability integrating "intelligence-warning-detection-response-recovery." Through the "offense promotes defense" mechanism, exercises compel defenders to shift from passive response to proactive defense, optimize defense strategies, perfect emergency plans, break down departmental barriers, and promote information sharing, thereby systemically honing and elevating the entire nation's cyber defense and deterrence capabilities.
- A "Training Ground" for Cultivating and Testing Top-Tier Cybersecurity Talent: The confrontation in cyberspace is ultimately a confrontation of talent. National-level exercises provide a superb platform for cybersecurity professionals to hone their technical and tactical skills, temper their psychological fortitude, and cultivate a strategic perspective and collaborative awareness in a real high-pressure environment. It is not only a "racetrack" for discovering and selecting cybersecurity leaders, tactical commanders, and top technical experts but also a core pathway for building a structurally sound, offensively and defensively capable, and well-tiered national cybersecurity talent pipeline.
1.3. Development and Historical Evolution
Globally, national-level cyber exercises can be traced back to military needs after the Cold War. The U.S. "Eligible Receiver" exercise in 1997 is a landmark event; it was the first to reveal the vulnerability of the U.S. Department of Defense's network systems to simulated attacks, giving rise to early concepts of cybersecurity readiness. Since then, exercises have gradually evolved from being purely military-internal to encompassing military-civilian integration and multinational collaboration.
China's series of national-level attack-defense exercises, represented by "Hynet" (护网), have continuously matured through practice. Their development trajectory exhibits the following distinct features:
- Scale and Intensity Increasing Annually: Participating units have expanded from a few core departments initially to cover government, military, and enterprise sectors nationwide. The intensity of attacks has evolved from exploiting common vulnerabilities to simulating targeted, persistent attacks launched by APT organizations.
- Deepening Real-Combat Orientation: The exercises have shifted from "notified" drills to "no notification, no path limits, no method limits" real-combat confrontations, with attack targets pointing directly at core business systems and production networks.
- Increasingly Clear Results-Orientation: Exercise outcomes are directly linked to a unit's annual security assessment and accountability, strongly driving proactivity in security investment, technological upgrades, and talent development.
After years of development, "Hynet" has become one of the largest and most influential national-level cybersecurity exercises globally, making indelible contributions to elevating China's overall cybersecurity posture and promoting industrial development.
1.4. Research Framework, Methods, and Objectives of This Report
This report aims to systematically deconstruct the complex system of national-level cyberspace security attack-defense exercises, providing theoretical support and practical guidance for the in-depth implementation of China's cyber power strategy. The research framework revolves around the main line of "Why exercise (Strategic Value) - Lessons from others (Global Models) - How to exercise (Top-Level Design & Technical Support) - Future directions (Innovative Trends & Strategic Foresight)."
This report primarily employs the following research methods:
- Case Study Method: In-depth analysis of typical global cases such as the U.S. "Cyber Flag," NATO's "Locked Shields," and Russia's "Internet Disconnection" drills to distill their successful experiences and strategic intentions.
- Comparative Research Method: Horizontally compares the differences in strategic objectives, organizational forms, and technical features of various national exercise models to provide references and insights for China.
- Forward-Looking Prediction Method: Combines lessons from real combat, such as the Russia-Ukraine conflict, to assess the disruptive impact of emerging technologies and operational styles like artificial intelligence, digital twins, and hybrid warfare on future exercises, and proposes corresponding strategies.
The core objective of this report is to construct a scientific, complete, and forward-looking theoretical framework for national-level attack-defense exercises and, based on this, to propose strategic, systematic, and actionable policy recommendations.
Chapter 2: Global Perspective—Practices and Insights from Major Countries' Cyber Exercises
2.1. The U.S. Model: Systematic, Globalized Cyber Readiness
The U.S. cyber exercise system fully embodies its "Defend Forward" and "Persistent Engagement" cyberspace strategies, aiming to deter conflict by operating outside its borders in collaboration with allies and proactively shaping the cyberspace battlefield environment.
"Cyber Flag": Led by the U.S. Cyber Command (USCYBERCOM), this is its highest-level annual joint military cyber exercise. Its core features include:
- Allied Coalition Warfare: The exercise typically invites over 20 allied and partner nations, including the "Five Eyes," NATO, and Indo-Pacific partners, to participate. It aims to refine command and control, intelligence sharing, and tactical coordination among multinational forces, acting as the "glue" for its cyber coalition warfare system.
- Highly Realistic Combat Scenarios: Exercise scenarios are directly designed to serve the U.S. military's global operational concepts. For example,
Cyber Flag 21-2simulated a cyberattack on U.S. logistical supply lines in the Indo-Pacific, whileCyber Flag 22-1re-enacted the SolarWinds supply chain attack, requiring participating forces to defend against real adversary TTPs. - "Hands-on-Keyboard" Training: The exercise emphasizes the practical operational skills of frontline cyber warriors, requiring them to execute real attack and defense operations on simulated Command and Control (C2) servers.
- Technical Platform Support: A key to its success is the Persistent Cyber Training Environment (PCTE). This is a cloud-based, globally accessible, standardized cyber range platform that can rapidly generate, deploy, and reset complex exercise environments, providing a unified training "gym" for global allies.
"Cyber Storm": Led by the Cybersecurity and Infrastructure Security Agency (CISA) under the Department of Homeland Security (DHS), this is a typical public-private partnership (PPP) exercise. Its focus is on protecting domestic critical infrastructure. Participants include federal, state, and local governments, as well as private sector companies (especially giants in finance, energy, and IT), aiming to drill national-level incident response, cross-departmental coordination, and information-sharing mechanisms to enhance the resilience of the entire society against large-scale cyberattacks.
2.2. The NATO Model: Collective Defense and Coordinated Response
NATO's exercise system is built around its Article 5 "collective defense" principle, emphasizing member states' coordinated response and mutual defense capabilities in the face of a cyberattack.
"Locked Shields": Hosted by the NATO Cooperative Cyber Defence Centre of Excellence (CCDCOE) in Tallinn, Estonia, it is recognized as the world's largest and most technically complex live-fire cyber defense exercise. Its core features include:
- Fine-grained Role Division: The exercise involves not only a Red Team (attackers) and Blue Teams (defenders) but also a Green Team (responsible for building and maintaining the complex range environment), a Yellow Team (responsible for situational awareness and intelligence assessment), and a White Team (responsible for organization, control, and evaluation), forming a complete ecosystem.
- Multi-dimensional, Comprehensive Confrontation: The exercise is not just a technical battle but a contest of comprehensive capabilities. Blue Teams must not only fend off technical attacks but also handle legal issues (e.g., the evidence chain for attribution), strategic communications (releasing information to the public, responding to media inquiries), and intelligence analysis tasks, holistically simulating the complex situation a nation faces during a cyberattack.
- Competitive Scoring Mechanism: The exercise uses a detailed scoring system to provide real-time scores and rankings for Blue Teams' performance in areas like service availability, quality of incident reporting, and legal and media responses. This competitive mechanism greatly stimulates countries' participation enthusiasm and sense of honor.
"Crossed Swords": This exercise is a companion to "Locked Shields," specifically designed to train and select Red Team members for "Locked Shields." It focuses purely on Offensive Cyber Operations (OCO) techniques and tactics and is the cradle for cultivating top-tier "cyber attackers" within the NATO system.
2.3. Russia and Other National Models
- Russia's Cyber Sovereignty Strategy and "Internet Disconnection" Drills: Facing continuous sanctions and cyber deterrence from the West, Russia has chosen a unique path centered on "digital sovereignty." Its "Sovereign Internet Law," passed and implemented in 2019, aims to establish a backup Domain Name System (DNS) and routing infrastructure independent of the global internet, known as "RuNet." To this end, Russia regularly holds nationwide "internet disconnection" drills.
- Core Objective of the Drills: To test whether Russia's domestic network infrastructure (government websites, banking systems, communication networks, etc.) can operate independently and stably in the extreme scenario of a physical or logical disconnection from the global internet.
- Strategic Intent: This reflects Russia's pursuit of absolute autonomous control and its bottom-line thinking and strategic determination to ensure the nation's information lifeline is not controlled by others in the worst-case scenario. This is a defensive exercise model with survival as its primary goal.
2.4. In-depth Analysis: The Russia-Ukraine Conflict's Real-World Test and Lessons for Cyber Exercises
The Russia-Ukraine conflict is the first large-scale modern hybrid war in human history to deeply integrate cyber warfare, physical warfare, and cognitive warfare. It acts as a mirror, reflecting the achievements and shortcomings of past cyber exercises and pointing the way for future ones.
- Real Combat is the Exercise, the Exercise is Real Combat: Months before the conflict erupted, cyberattack activities against Ukraine had already sharply increased. Cyberspace confrontation became an important part of shaping the battlefield environment and pre-war preparations. The line between exercises and real combat became unprecedentedly blurred.
- Hybrid Warfare is the New Norm: During the war, cyberattacks no longer existed in isolation. Attacks on the Viasat satellite communication network (physical paralysis) were combined with destructive wiper malware (like
WhisperGateandAcidRain) (digital destruction), and large-scale disinformation campaigns and psychological warfare (cognitive domain attacks), forming a multi-layered hybrid strike. - Critical Infrastructure is the Focal Point: The cyberattacks from both sides consistently centered on government, energy, finance, media, and transportation sectors. This once again confirms that CII is the center of gravity in cyber warfare, and its defensive resilience is directly related to a nation's war potential and social stability.
- New Forces are Reshaping the Battlefield: The intervention of commercial companies and civilian forces has profoundly changed the face of cyber warfare. SpaceX's "Starlink" system provided crucial communication support for Ukraine, while civilian hacker groups like the "IT Army of Ukraine" launched large-scale, crowdsourced DDoS attacks against Russia.
- Strategic Lessons for Exercises:
- Must Strengthen Hybrid War Simulation: Future exercises can no longer be limited to pure cyber attack-defense. They must incorporate elements like physical destruction, electromagnetic interference, and cognitive domain confrontation (e.g., social media opinion manipulation, deepfake video attacks).
- Must Pay High Attention to Supply Chain Security: Supply chain attacks similar to SolarWinds have been frequent in the conflict. Exercises need to focus on testing the risks associated with dependencies on third-party software, open-source components, and hardware suppliers.
- Must Include Non-State Actors in Considerations: Exercises need to simulate the roles that commercial tech giants and civilian hacker organizations might play in a conflict and study response strategies.
- Must Enhance Data Security: The proliferation of destructive wipers indicates that data backup and rapid recovery capabilities are key to survival in wartime.
2.5. Comparative Analysis and Lessons for China
| Model | Strategic Objective | Core Feature | Guiding Philosophy |
|---|---|---|---|
| U.S. Model | Maintain global cyber hegemony, defend forward | Allied coalition warfare, public-private partnership, technology-driven | Proactive offense, control global cyberspace |
| NATO Model | Collective security, coordinated defense | Multi-dimensional confrontation, standardized, competitive | Joint defense, enhance alliance-wide resilience |
| Russian Model | Defend cyber sovereignty, ensure survival | State-led, autonomous control, isolation testing | Absolute sovereignty, bottom-line thinking, independent survival |
Each country's exercise model is a direct reflection of its national strategy. The U.S. pursues global offensive capabilities and alliance leadership; NATO focuses on collective defense and standardized responses for its members; Russia prioritizes the independence and survival of its cyber sovereignty.
For China, we should draw on the strengths of all, integrate and innovate, and build an exercise system with Chinese characteristics:
- Learn from the systematic organization and technical platforms of the U.S. and NATO: Emulate their fine-grained role division, multi-dimensional scenario design, standardized evaluation systems, and advanced cyber range technology.
- Absorb Russia's strategic focus on cyber sovereignty: Adhere to the principle of autonomous control and make ensuring the survivability of critical information infrastructure under extreme conditions one of the core objectives of our exercises.
- Base on national conditions, focus on real combat: Closely align exercise scenarios with the real security threats China faces and the latest combat lessons from events like the Russia-Ukraine conflict. Make supply chain security, hybrid warfare confrontation, and data security top priorities for exercises, serving the strategies of becoming a cyber power and the overall national security concept.
Chapter 3: Top-Level Design—The Scheme System and Organizational Implementation of National Attack-Defense Exercises
3.1. Core Principles of Exercise Design
The top-level design of national-level attack-defense exercises must adhere to a set of core principles to maximize their strategic value.
- Goal-Oriented Principle: The primary task of an exercise is to serve the national cybersecurity strategy. At the outset of planning, clear, specific, and measurable exercise objectives must be defined. For example, an objective could be "to reduce the Mean Time to Respond (MTTR) to new types of ransomware for national CII units by 20%," or "to test the effectiveness of the financial industry's business continuity plans during a large-scale DDoS attack." Clear goals are the benchmark for all subsequent design and evaluation.
- Realism-Focused Principle: The success or failure of an exercise depends on its proximity to the real world. The design must strive for high fidelity in five aspects:
- Simulated Threat Actor: Based on the latest threat intelligence, simulate the profile, motives, and common TTPs of specific APT organizations.
- Simulated Environment: Replicate the target unit's real network architecture, business systems, and data flows within the cyber range.
- Simulated Tools: Use tools (like Cobalt Strike) and techniques actually employed by attackers in the real world.
- Simulated Target: The attack targets should be core systems with real business value, not irrelevant test machines.
- Simulated Scenario: The scenario should be a multi-stage, multi-layered, complex attack chain, not a single vulnerability exploitation.
- Systemic Confrontation Principle: The exercise should not be a "Red Team show-off" or a "Blue Team equipment showcase," but a comprehensive test of the entire defense system. The evaluation should focus on the defender's overall performance across the entire Kill Chain—before the attack (prediction and defense), during the attack (detection and response), and after the attack (recovery and attribution)—testing the combined operational effectiveness of "people, technology, and processes."
3.2. Full Lifecycle Management of the Exercise
A mature national-level exercise should follow a complete, closed-loop lifecycle management process to ensure procedural standardization and the effectiveness of outcomes.
- Initiation (Planning) Phase:
- Form a Leadership Group and Working Groups: Clearly define the responsibilities of organizers, hosts, directors, expert panels, participating units, etc.
- Determine Exercise Objectives and Scope: Based on national strategic needs, define the core objectives, scope of participating units, key scenarios, and "red line areas" that are off-limits to attack.
- Develop an Overall Plan and Budget: Prepare a detailed exercise plan, timeline, resource requirements, and budget.
- Preparation (Pre-war) Phase:
- Asset Inventory and Risk Assessment: Participating Blue Teams conduct a comprehensive inventory of network assets, business impact analysis, vulnerability scanning, and penetration testing to get a clear picture of their state.
- Security Hardening and Policy Optimization: Based on the risk assessment, carry out system patching, security policy tuning, access control strengthening, and other rectification work.
- Personnel Training and Plan Drills: Train Blue Team personnel on security awareness, tool usage, and emergency procedures, and conduct tabletop exercises for key emergency plans.
- Execution (Combat) Phase:
- Live Confrontation: The Red Team launches real attacks against the Blue Team's target network within the established rules.
- Process Control: The White Team (directors) monitors the attack-defense situation in real time, injects unexpected events (e.g., "a senior executive's account has been compromised") according to the plan, controls the exercise tempo, and prevents situations from getting out of hand.
- Real-time Response: The Blue Team operates around the clock, monitoring, analyzing, judging, containing, eradicating, and recovering from attack activities.
- Support Phase:
- Technical Platform Support: Ensure the stable operation of the cyber range, situational awareness platform, and command and communication systems during the exercise.
- Intelligence Support: Provide necessary external intelligence support to the Blue Team through threat intelligence platforms to aid their analysis.
- Risk Control: Establish a "circuit breaker" mechanism to immediately halt relevant attack activities if the exercise has an unacceptable impact on real business operations.
- Summary and Evaluation Phase:
- Comprehensive After-Action Review (AAR): Organize a review meeting with both attack and defense teams, directors, and expert panels to detail the attack paths, defensive highlights, and shortcomings.
- Report Writing: Produce a summary report containing a list of issues, cause analysis, and improvement recommendations.
- Rectification and Capability Consolidation: Issue rectification notices and track their implementation. Convert the effective experiences gained during the exercise into Standard Operating Procedures (SOPs) and a knowledge base to achieve a closed loop of capability improvement.
3.3. Core Elements: Scenario Construction and Design
The scenario is the soul of the exercise, and its quality directly determines the exercise's value. Designing an excellent scenario is a complex engineering task that combines technical insight, tactical imagination, and artistic creativity.
- Scenario Sources:
- Driven by Real Threat Intelligence: Based on the latest activity reports on APT organizations targeting our country, provided by national-level threat intelligence centers.
- Re-enactment of Major Security Incidents: Replicating globally significant events like the SolarWinds supply chain attack, Log4Shell exploitation, and ransomware attacks.
- Mapping of Geopolitical Conflicts: Simulating cyberattacks that might be encountered in specific geopolitical contexts (e.g., trade friction, regional conflicts).
- Pre-emptive Drills for Forward-Looking Technical Risks: Conducting drills for potential future threats like AI security, quantum computing decryption, and IoT botnets.
- Scenario Focus: Scenarios should focus on national critical information infrastructure that has a significant impact on the national economy and people's livelihood, especially in areas with a "domino effect," such as:
- Financial Systems: Simulating attacks on core trading and clearing systems, intended to create market panic.
- Energy and Power Grids: Simulating attacks similar to the 2015 Ukraine power outage, aimed at causing large-scale blackouts.
- Transportation Hubs: Simulating attacks on air traffic control and high-speed rail dispatching systems, intended to paralyze transport.
- Communication Networks: Simulating attacks on backbone networks and DNS systems, aimed at causing widespread internet outages.
- Defense Industry: Simulating attacks to steal core weapon system design blueprints or disrupt production lines.
- Advanced Scenario Example: A typical national-level advanced scenario might include the following attack chain:
- Initial Compromise: Plant a backdoor in the update package of office software by attacking a software vendor (supply chain attack).
- Lateral Movement: Use the backdoor to enter a CII unit's office network, then use a spear-phishing email to steal an operator's VPN account to access the production network.
- Privilege Escalation: Exploit a "Zero-Day" vulnerability to gain the highest privileges on the domain controller.
- Objective Achievement: Lurk in the core business database, steal sensitive data, and plant a logic bomb and ransomware.
- Coordinated Strike: Detonate the logic bomb at a predetermined time while spreading false information on social media that "a financial institution's core data has been leaked" (cognitive domain attack), triggering a public run on the bank.
3.4. Legal Regulations and Ethical Boundaries
National-level exercises are immensely powerful and must operate under strict legal authorization and ethical frameworks to ensure their benefits outweigh their risks.
- Legal Authorization: The initiation of an exercise must be formally authorized by the highest national cybersecurity authority to establish its legality.
- Rules of Engagement (RoE): Extremely detailed RoE must be established, clearly specifying the techniques attackers can use, the permissible scope of targets, prohibited methods (e.g., threats to personal safety), and the conditions under which an attack must be immediately halted. The RoE are the "traffic laws" of the exercise.
- Risk Control: High-risk operations that could affect production systems must undergo graded approval by the director team. They should preferably be tested in a digital twin environment first to assess their impact before implementation.
- Data Protection and Privacy: The exercise may involve access to sensitive personal information and business data. Technical measures like data desensitization and anonymization must be taken, and strict confidentiality agreements must be signed to ensure data is not leaked or misused, strictly complying with relevant laws and regulations such as the Cybersecurity Law, Data Security Law, and Personal Information Protection Law.
Chapter 4: Technological Cornerstone—Core Technologies, Cyber Ranges, and Tool Platforms in Exercises
4.1. Cyber Range: A High-Fidelity Digital Twin Battlefield
A Cyber Range is an indispensable infrastructure for conducting national-level attack-defense exercises. It provides a secure, isolated, highly realistic, and controllable "digital twin battlefield" for the exercises.
- Technical Architecture: Modern cyber ranges are generally based on a cloud computing architecture, with a core technology stack that includes:
- Virtualization and Containerization: Using virtualization technologies like VMware and KVM, and container technologies like Docker and Kubernetes, to enable rapid orchestration, elastic scaling, and second-level resets of computing, storage, and network resources. This provides independent training environments for hundreds or even thousands of participants.
- Software-Defined Networking (SDN): Through SDN technology, any complex network topology can be flexibly and dynamically constructed, simulating the intricate network environments of multinational corporations, metropolitan area networks, or even national backbones.
- Key Technologies:
- Business Simulation Technology: This is the "soul" of the cyber range. It's not just about starting a bunch of virtual machines, but about simulating real business applications (like a bank's transaction system or a power plant's SCADA system), user behaviors (like employees sending emails or browsing the web), and data flows. Only a "living" range can effectively test a defender's detection and analysis capabilities.
- Traffic Generation Technology: To simulate a realistic network environment, the range needs to be able to generate massive amounts of background traffic with characteristics highly similar to real internet traffic. Attack traffic is hidden within this "noise," greatly increasing the difficulty for the Blue Team to discover it.
- Digital Twin Technology: This is the highest stage of cyber range technology development. It aims to create a digital mirror of a physical world's critical infrastructure (like a substation or a production line) that is identical in function, behavior, and state. On this digital twin, risk-free attack testing, vulnerability validation, tactical wargaming, and effect assessment can be conducted, providing decision support for the security of the physical world.
4.2. Attack (Red Team) Technology and Arsenal
The Red Team's mission is to simulate the most advanced, well-resourced, state-level attackers. Their technology and tools represent the "state of the art" in the current field of cyberattacks.
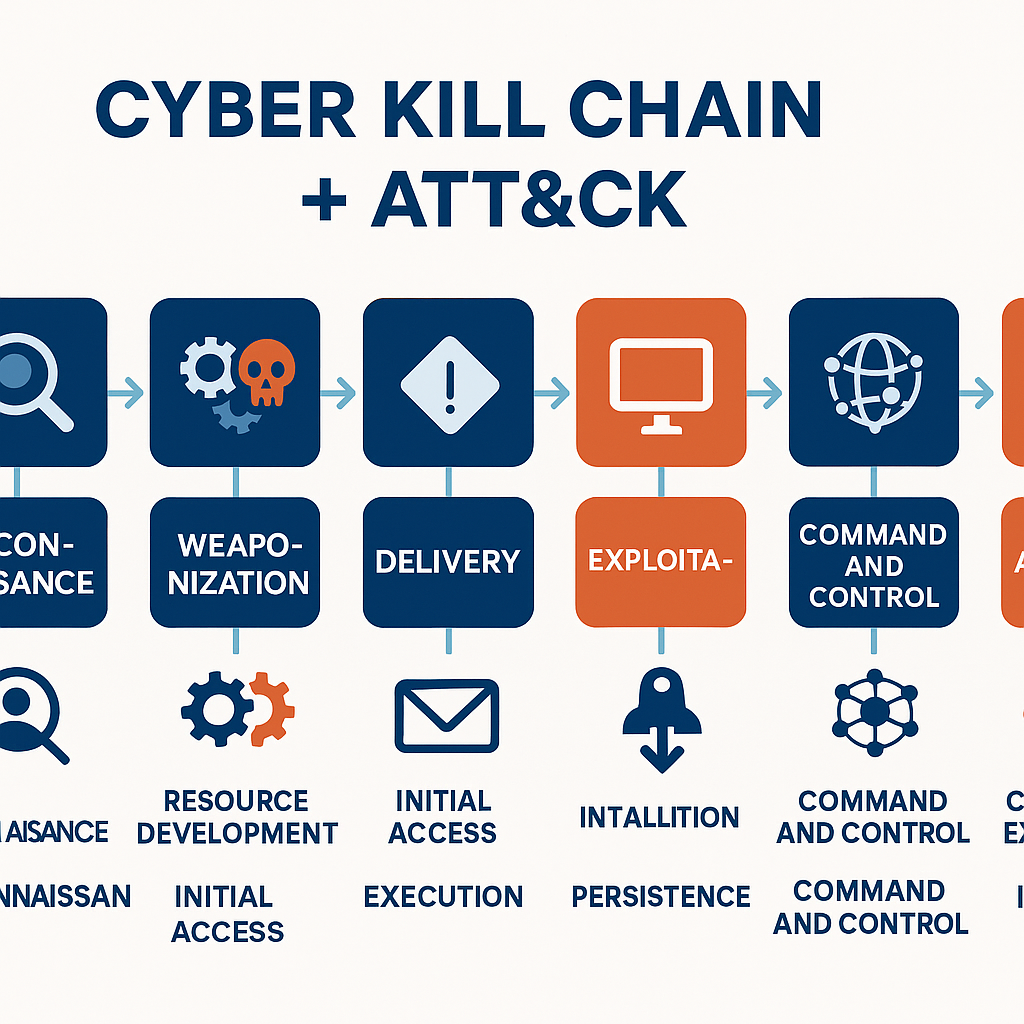
Figure Caption 4.1: This is a common model for modern cyberattacks, integrating the classic "Cyber Kill Chain" with the more granular
MITRE ATT&CKframework. In an exercise, the Red Team (attackers) uses such frameworks to systematically plan the complete attack path (TTPs)—from reconnaissance and weaponization to delivery, command and control, lateral movement, and achieving objectives—to simulate the operational methods of real-world Advanced Persistent Threats (APTs).
| Category | Typical Tools/Technologies | Function |
|---|---|---|
| Attack Frameworks | Cobalt Strike, Metasploit, Empire | Provide integrated C2, privilege escalation, lateral movement, and persistence functions for the post-exploitation phase. |
| Tactical Knowledge Base | MITRE ATT&CK Framework | The Red Team uses ATT&CK as a "tactical map" and "attack playbook" to systematically plan and execute attack chains (TTPs) that mimic real APT organizations. |
| Automation Tools | SQLMap, Nmap, Burp Suite | Used for automated vulnerability scanning, SQL injection, and web application penetration testing to increase the breadth and efficiency of attacks. |
| Customized Weapons | Self-developed Rootkits, 0-day exploits, polymorphic malware | Develop custom attack payloads that cannot be detected by conventional means, targeting specific targets or defensive products. |
| Integrated Methods | Social engineering, spear-phishing, watering hole attacks, supply chain poisoning | Combine non-technical means to achieve initial breach by targeting the weakest link in the defense system—the "human" element or the trust chain. |
4.3. Defense (Blue Team) Technology and Arsenal
The Blue Team represents the best practices of a modern, defense-in-depth system. Its arsenal is typically built around a Next-Generation Security Operations Center (Next-Gen SOC).
- Core Detection and Response Technologies: Modern SOCs commonly use a "visualization triad" as their core technical support:
- SIEM (Security Information and Event Management): As the central hub for log aggregation and analysis, it collects logs from all network devices and discovers suspicious events through correlation analysis rules.
- EDR (Endpoint Detection and Response): Deployed on employee computers and servers, it focuses on endpoint behavior and can effectively detect advanced threats like fileless attacks and in-memory malware.
- NDR (Network Detection and Response): Through deep packet inspection (DPI) and behavioral analysis of network traffic, it discovers network-level anomalies such as lateral movement and C2 communications.
- XDR (Extended Detection and Response): As an evolution of SIEM, XDR aims to break down the "data silos" between different security products (endpoint, network, cloud, etc.), automatically correlating multi-source alerts into complete attack storylines, thereby greatly improving analysis efficiency.
- Key Defensive Platforms and Architectures:
- SOAR (Security Orchestration, Automation, and Response): Used to automate the execution of standardized incident response procedures (Playbooks). For example, upon detecting ransomware, SOAR can automatically isolate the infected host, block malicious IPs, and notify administrators.
- Threat Intelligence Platform (TIP): Integrates internal and external threat intelligence to provide "ammunition" (like malicious domains, virus hashes) for security devices and to provide security analysts with background information on attackers to aid their judgment.
- "Zero Trust" Architecture: As a new generation of security philosophy, its core idea is "never trust, always verify." In an exercise, the Blue Team will build a network based on Zero Trust principles, subjecting every access request to strict identity verification and permission checks, effectively containing attackers' lateral movement.
4.4. Control (White/Purple Team) and Evaluation Platforms
- White Team (Directors): The "brain" and "referee" of the exercise. The White Team has a "God's eye view" through a Control Platform, monitoring the real-time confrontation status, network traffic, and system states of both Red and Blue teams. The White Team can inject specific events ("a system suddenly fails," "a forged email from the CEO is received") to adjust the difficulty and pace of the exercise and adjudicate and record the scores of both sides.
- Purple Team (Analysts): The "bridge" and "catalyst" connecting the Red and Blue teams. A Purple Team usually consists of experienced attack and defense experts. Its goal is not to win the confrontation but to enhance the overall value of the exercise. The core working model of a Purple Team is:
- The Red Team executes an attack.
- The Purple Team and the Blue Team analyze together: Was this attack detected? If not, why? Was it due to a lack of logs, ineffective detection rules, or human negligence?
- The Purple Team helps the Blue Team immediately adjust its defense strategy or add detection rules.
- The Red Team attempts the attack again under the new defense strategy. This tight loop of "attack-analyze-improve-re-attack" allows the Blue Team's capabilities to be improved in real-time and rapidly during the exercise.
4.5. Frontier Technology Integration: The Double-Edged Sword of AI and Large Models
Artificial Intelligence (AI), especially Large Language Models (LLMs), is penetrating every aspect of cyber attack and defense with unprecedented depth and breadth, presenting a typical "double-edged sword" effect.
| Application Area | AI for Attack | AI for Defense |
|---|---|---|
| Reconnaissance | Automated asset discovery, intelligent analysis of target organization structures to find social engineering breakthroughs. | Automated asset inventory and risk assessment, predicting potential attack surfaces. |
| Attack Execution | LLMs generating highly realistic phishing emails and social engineering scripts; AI automating vulnerability discovery and exploitation (Fuzzing). | Using User and Entity Behavior Analytics (UEBA) to detect anomalous account activity and insider threats. |
| Malware | AI generating polymorphic, evasion-capable malware to bypass traditional antivirus detection. | Machine learning-based malware detection models to identify unknown virus families. |
| Command & Control | AI planning optimal attack paths, achieving automated lateral movement and privilege escalation. | AI intelligently correlating multi-source alerts, automatically tracing attack chains, and reducing false positives. |
| Decision Support | - | LLMs assisting security analysts: Querying massive logs with natural language, automatically generating incident analysis reports, recommending remediation plans. |
Future exercises must fully simulate AI-driven attacks while also testing and strengthening AI as a core capability of the defense system. How to effectively harness the power of AI while preventing its misuse is a common challenge for all participants.
Chapter 5: Collaborative Warfare—Cross-Departmental, Cross-Domain Linkage and Command Mechanisms
5.1. Composition and Role Positioning of Participating Forces
The success of a national-level exercise depends on a diversified participation system with clear division of labor and efficient collaboration.
| Role | Codename | Primary Composition | Core Responsibilities and Positioning |
|---|---|---|---|
| Attacking Force | Red Team | Professional penetration testing companies, researchers from cybersecurity vendors, university teams, national-level professional attack units | "Whetstone": Simulates the most advanced, state-backed APT organizations, using various means to conduct continuous, realistic attacks on the Blue Team to discover the limits and weaknesses of its defense system. |
| Defending Force | Blue Team | IT and security teams from critical information infrastructure operators, key government departments, large enterprises, and their security service providers | "Frontline": Responsible for real-time monitoring, analysis, response, and handling. They bear the main pressure and are the core force for testing the effectiveness of the defense. |
| Director Force | White Team | Exercise organizers, industry regulators, third-party assessment agencies, senior technical experts | "Referee and Director": Responsible for setting rules, planning scenarios, monitoring the overall exercise, controlling the tempo, adjudicating results, and evaluating effectiveness, ensuring the exercise proceeds smoothly on its intended track. |
| Analysis & Collaboration Force | Purple Team | Experienced top-tier attack-defense experts, usually independent of Red and Blue teams | "Glue and Enabler": Does not directly participate in the confrontation but acts as a communication bridge between Red and Blue. Helps the Blue Team understand Red's attack methods and optimize defenses, while providing feedback to the Red Team on the effectiveness of defense strategies. Its goal is to maximize the knowledge transfer and capability improvement value of the exercise. |
5.2. Command System Construction
An efficient command system is key to ensuring unified dispatch and agile response during complex confrontations in an exercise.
- Centralized and Unified Command Center: Typically, a three-tier command system is established: national, industry, and unit level. The national-level exercise headquarters acts as the supreme decision-making body, responsible for strategic decisions and cross-departmental resource allocation. Each industry主管單位 sets up a sub-command center, and each participating Blue Team establishes a field command post.
- Clear and Efficient Command Chain: A "vertically through, horizontally linked" command chain is established. Vertically, it ensures that commands from the headquarters can be quickly and accurately transmitted to frontline defenders. Horizontally, it ensures that different departments and units can collaborate when facing cross-domain attacks.
- Agile Command Model: The fast-paced nature of cyber attack and defense makes traditional hierarchical command models inadequate. Exercises are pushing a transformation toward a flat, networked agile command model, granting frontline commanders greater autonomy in decision-making to achieve "second-level response."
5.3. Cross-Domain Collaboration Mechanisms
Modern cyberattacks are often cross-domain and multi-dimensional, making the construction of collaboration mechanisms central to the success of an exercise.
- Military-Civilian Integration and Public-Private Partnerships (PPP): Exercises are the best practice platform for breaking down barriers between the military, civilians, government, and enterprises. National intelligence agencies, military cyber forces, public security cyber units, key enterprises, research institutes, and cybersecurity companies come together, forming a de facto "cybersecurity united front." For example, national intelligence agencies share targeted threat warnings with enterprise Blue Teams, who in turn report new attack methods they discover, creating a virtuous cycle.
- Intra-Industry and Inter-Industry Collaboration: Exercises test not only individual units but also the linkage capabilities of entire industries. A financial industry exercise will test the coordinated response among banks, securities firms, and insurance institutions. A cross-industry exercise might simulate a scenario where an attack on the power grid leads to a power outage at a bank's data center, testing the effectiveness of cross-industry emergency plans.
- International Cooperation and Exchange: As cyber threats become globalized, selectively conducting joint exercises with friendly nations becomes increasingly important. By participating in or hosting international exercises, we can learn from other countries' advanced organizational experience and tactical thinking, share best practices for dealing with transnational cybercrime and APT organizations, and jointly build a community with a shared future in cyberspace.

Figure Caption 5.1: Modern cyber defense is no longer a solitary fight for any single entity. It requires building a collaborative defense system that includes the military, government, critical infrastructure enterprises, security research institutes, and network infrastructure companies. One of the core goals of national-level exercises is to test and strengthen this "military-civilian integrated, multi-party collaborative" linkage, command, and intelligence-sharing mechanism, forming a "nationwide coordinated" overall defense force.
5.4. Information Sharing and Intelligence Flow
Information and intelligence are the "lifeblood" of cyber warfare. The efficiency of their sharing and flow mechanisms directly determines the success or failure of collaborative operations. In the real world, "data silos" and "intelligence barriers" are common due to departmental interests, data ownership, and legal restrictions.
One of the core objectives of an exercise is to forcibly break down these barriers in a controlled environment.
- Establish a Unified Intelligence Sharing Platform: During an exercise, a temporary, secure intelligence sharing platform is usually established. All participating units upload indicators of compromise (such as malicious IPs, domains, file hashes) to the platform in real-time.
- Standardize Intelligence Formats: Adopt international standards like STIX (Structured Threat Information eXpression) and TAXII (Trusted Automated eXchange of Intelligence Information) to ensure that intelligence generated by security devices from different vendors and systems can be understood and utilized by each other.
- Drive Mechanism Optimization through Exercises: Exercises expose the bottlenecks and breakpoints in existing intelligence sharing processes (e.g., lengthy approval processes, inefficient reporting channels). This pushes relevant units to optimize their real-world processes after the exercise, establishing more efficient and automated routine threat intelligence sharing mechanisms.
Chapter 6: Value Assessment—Quantitative Evaluation and Strategic Impact of Exercise Effectiveness
6.1. Establishing a Scientific Evaluation Metrics System
The value of an exercise cannot be judged solely on subjective feeling. A scientific, quantitative, and multi-dimensional Key Performance Indicator (KPI) system must be established to objectively measure effectiveness and guide improvement. The evaluation should cover at least three dimensions: defense, attack, and organization.
Table 6.1: Core Evaluation Metrics for National-Level Attack-Defense Exercises (Example)
| Evaluation Dimension | Primary Metric | Secondary Metrics (KPIs) | Metric Definition |
|---|---|---|---|
| Blue Team (Defender) Effectiveness | Detection Capability | Mean Time to Detect (MTTD) | The average time from when an attack occurs to when it is first effectively discovered by the Blue Team. Lower is better. |
| Attack Coverage/Discovery Rate | The percentage of Red Team attack steps (TTPs) discovered by the Blue Team out of the total executed. Higher is better. | ||
| Response Capability | Mean Time to Respond (MTTR) | The average time from detecting an attack to completing the full process of containment, eradication, and recovery. Lower is better. | |
| Alert Accuracy Rate | The proportion of valid attack alerts reported by the Blue Team out of the total number of alerts. Higher is better. | ||
| Defensive Resilience | Core Business Continuity | The percentage of time that core business systems remained available during the attack. Higher is better. | |
| Vulnerability Remediation Rate | The proportion of vulnerabilities discovered during the exercise that were fixed within the specified time. Higher is better. | ||
| Red Team (Attacker) Capability | Penetration Efficiency | Mean Time to Breach | The average time from the start of the attack to gaining an initial foothold in the target network. Lower is better. |
| Objective Achievement Rate | The percentage of preset core targets successfully compromised by the Red Team. Higher is better. | ||
| Stealth Capability | Dwell Time | The total time spent lurking inside the target network before being discovered. Longer is better. | |
| Attack Stealthiness | The difficulty for the Blue Team to detect the attack actions (assessed by the White and Purple Teams). Higher is better. | ||
| Organizational & Collaborative Effectiveness | Command & Decision | Command & Control Efficiency | The average time and accuracy from when a command is issued to when it is executed by the frontline. Shorter time, higher accuracy is better. |
| Decision Quality | The proportion of correct decisions made at critical junctures (e.g., whether to disconnect from the internet, whether to counter-attack). Higher is better. | ||
| Processes & Mechanisms | Intelligence Sharing Timeliness | The average time from when threat intelligence is generated by one unit to when it is received and utilized by others. Shorter is better. | |
| Process Maturity | The standardization, automation, and effectiveness of processes like incident response and information reporting (assessed by the White Team). Higher is better. |
6.2. Evaluation Methodologies and Models
- After Action Review (AAR): This is the most crucial and valuable session after an exercise. An AAR is not a "blame session" but a structured discussion conducted in a "no-blame" atmosphere. All participants jointly review four key questions:
- What was supposed to happen?
- What actually happened?
- Why was there a difference?
- What did we learn and how can we improve? Through the AAR, both sides can exchange perspectives. The Blue Team learns about attack paths they missed, and the Red Team learns which of their actions exposed their tracks.
- Capability Maturity Assessment Models: Models like CMMI (Capability Maturity Model Integration) and the NIST Cybersecurity Framework (CSF) can be used to assess the security capability level of participating units. By conducting assessments before and after the exercise, the unit's progress in the five capability domains—Identify, Protect, Detect, Respond, Recover—can be quantitatively demonstrated.
- Wargaming and Game Theory Analysis: For key confrontational nodes in the exercise, game theory models can be introduced to analyze the strategy choices and payoffs of the Red and Blue teams under asymmetric information conditions. This allows for a deeper understanding of the nature of the confrontation and the deduction of superior attack and defense tactics.
6.3. Transformation and Application of Exercise Outcomes
The ultimate purpose of an exercise is not the "show" but the "training." Its value lies in transforming the "experience" and "lessons" gained into the organization's lasting "capabilities."
- Closed-Loop Issue Management: All issues discovered during the exercise (technical vulnerabilities, management flaws, process breakpoints) must be documented and managed in a dedicated tracking system. Each issue should have a clear responsible person, a deadline for rectification, and verification criteria, forming a closed-loop management process of "discover-assign-rectify-verify-close."
- Knowledge Consolidation and Codification: The effective defense tactics, emergency plans, detection rules, and collaborative processes proven in the exercise should be refined and codified into the organization's Standard Operating Procedures (SOPs), technical specifications, and knowledge base. This transforms the practical experience of a few elites into a collective capability that the entire organization can follow and inherit.
- Technological Innovation and Industry Drive: The defensive weaknesses exposed in exercises are the best "demand pull" for cybersecurity technology innovation. For example, if an exercise reveals that traditional firewalls cannot defend against a certain type of attack, this will directly drive the demand for procurement and R&D of next-generation firewalls or Zero Trust products, thereby promoting technological advancement in the entire cybersecurity industry.
6.4. Strategic Impact Assessment
In addition to direct technical and management improvements, national-level attack-defense exercises also have profound strategic impacts:
- Promoting the Improvement of Policies and Regulations: The common and industry-wide problems exposed in exercises are an important basis for the state to amend relevant cybersecurity laws and regulations and to issue industry supervision policies.
- Fostering a Healthy Industrial Ecosystem: Exercises provide a practical testing ground for cybersecurity products and services, where "the proof of the pudding is in the eating." This fosters a survival-of-the-fittest environment, allowing truly capable companies to stand out and lead the healthy development of the industry.
- Enhancing National Cybersecurity Awareness: Through appropriate publicity of exercise results, the severity of cybersecurity threats can be vividly demonstrated to the public, raising the cybersecurity awareness and sense of responsibility of the entire society, especially for personnel in key positions.
- Forming National-Level Deterrence: Regularly holding high-level national attack-defense exercises is itself a strategic signal, demonstrating the country's solid cyber defense capabilities and its determination to defend its cyber sovereignty, thereby forming an effective cyberspace deterrence.
Chapter 7: Innovative Evolution—Models and Trends of New-Generation Cyber Attack-Defense Exercises
7.1. Upgrading Exercise Philosophy: The Leap from Compliance to Real Combat
The guiding philosophy of national-level attack-defense exercises is undergoing a profound transformation, following a clear three-step evolutionary path:
- Compliance-Driven: In the early stages, the main purpose of exercises was to meet the compliance requirements of regulatory authorities. Participating units often had a "handing in homework" mentality, leading to formalism and scripted exercises.
- Capability-Driven: As understanding deepened, the core objective of exercises shifted to genuinely testing and improving security capabilities. Participating units began to proactively use exercise opportunities to identify their own weaknesses and guide their investments and construction based on "capability improvement."
- Threat-Driven: This is the current and future direction. All aspects of exercise design are tightly centered on real-world threats, with the sole criterion being "whether one can defeat real adversaries in a confrontation." The exercise is real combat, and real combat is the test, pursuing an infinite approximation of real cyber warfare.
7.2. Scenario Expansion: Covering Emerging Technologies and Threat Areas
The boundaries of the future cyber battlefield will extend far beyond traditional IT networks. Exercise scenarios must also expand to all digitally existing domains.
- Industrial Internet (OT/ICS) Security: Exercises will simulate attacks on industrial control systems of power plants, dams, and smart manufacturing production lines, such as tampering with PLC (Programmable Logic Controller) logic to cause physical shutdowns, testing the security protection capabilities in converged OT/IT environments.
- Artificial Intelligence (AI) Security: Exercises will introduce attack-defense scenarios targeting AI models and algorithms. For example, the Red Team might use "data poisoning" to contaminate training data, causing the AI model to make incorrect decisions, or use "adversarial examples" to deceive systems like facial recognition or autonomous driving. The Blue Team will need to deploy defense mechanisms capable of detecting such AI attacks.
- Supply Chain Security: Given the profound impact of incidents like SolarWinds, supply chain attacks will become a core scenario in future exercises. Exercises will simulate attacks launched from upstream links such as software developers, open-source code repositories, and third-party service providers, testing the participating units' supply chain risk management and defense-in-depth capabilities.
- Cloud-Native and DevSecOps Security: With the popularization of cloud adoption and containerized deployment, exercises will focus on new attack surfaces like cloud environment misconfigurations, container escapes, and API security. They will also "shift left" security exercises into the software development lifecycle, integrating attack-defense testing into the DevSecOps process.
7.3. Model Innovation: "Virtual-Real Integration" and "All-Domain Linkage"
- Multi-Domain Operations (MDO) Exercises: Future high-level exercises will break the "cyberspace" dimension wall, achieving deep linkage with the physical, electromagnetic, and cognitive spaces to simulate true "Hybrid Warfare."
- A typical multi-domain scenario might be as follows: The Red Team first paralyzes a city's power grid dispatching system via a cyberattack (Cyber Domain), simultaneously deploys a drone swarm to physically damage key substations (Physical Domain), and jams its emergency communications (Electromagnetic Domain). Finally, it spreads panic-inducing information on social media that "the city will face an indefinite blackout," causing social unrest (Cognitive Domain). This exercise model poses an unprecedented challenge to a nation's comprehensive emergency command capabilities.
7.4. Operational Revolution: Moving Towards "Continuous Exercises"
The traditional "once a year" centralized exercise model is no longer frequent or comprehensive enough to cope with 24/7, non-stop real-world threats. The operational model of exercises is moving towards being routine, automated, and continuous.
- Persistent Cyber Training Environment (PCTE): Building a "permanently online" national-level cyber range platform similar to the U.S. military's PCTE. This platform can provide standardized, on-demand, 24/7 available training and exercise environments for government and enterprise units and security personnel across the country, enabling "practice anytime, anywhere."
- Routine Red-Blue Teaming and Breach and Attack Simulation (BAS): Breaking down large-scale annual exercises into fragmented, daily attack-defense activities. By introducing Breach and Attack Simulation (BAS) platforms, the existing defense system can be continuously and automatically validated, achieving "training through combat" and elevating security capabilities from "static compliance" to "dynamic confrontation."
- Automated Unmanned Attack and Defense: Exploring the use of AI to automate attack and defense. For example, deploying AI-driven automated Red Team tools to conduct non-stop simulated attacks on the network, while also deploying AI-driven automated Blue Teams (like SOAR) to achieve automatic detection, analysis, and response to attacks. This is the ultimate goal of achieving "24/7 unmanned exercises."
7.5. Methodological Evolution: The Rise and Value of "Purple Teaming" Culture
"Purple Teaming" is the most significant methodological innovation to emerge in new-generation cyber attack-defense exercises in recent years. Its core is to break the binary, "zero-sum game" mentality of traditional Red vs. Blue confrontation.
- Core Concept: A Purple Team is not an independent team but a collaborative culture and workflow. It emphasizes that the Red and Blue teams are no longer "back-to-back" adversaries but "shoulder-to-shoulder" comrades.
- Working Model: In a Purple Teaming model, after executing each attack step, the Red Team proactively communicates with the Blue Team, informing them of the attack methods and paths. Both sides jointly analyze why the Blue Team failed to detect or block the attack and immediately adjust and optimize the Blue Team's defense strategies, detection rules, or response processes. Then, the Red Team launches the next round of attacks based on the new defense posture.
- Value Leap: This tight collaboration and instant feedback loop shifts the goal of the exercise from "finding out how many vulnerabilities the Blue Team has" (problem discovery) to "how much the Blue Team's defense capability has improved by the end of the exercise" (jointly solving problems). It transforms the exercise from a one-time "exam" into a highly efficient, interactive "on-site training session," greatly enhancing the efficiency of knowledge transfer and the ultimate value of the exercise.
Chapter 8: Command Center—A Combat-Oriented Cyberspace Operations Command Platform
8.1. Platform Positioning: The "Brain" and "Nervous System" of Cyberspace
In national-level cyber confrontations, a powerful command platform is a prerequisite for victory. This platform is no longer a traditional "Security Operations Center (SOC)" or "Situational Awareness Platform" that passively displays alerts. Instead, it is a combat-oriented, proactive Cyberspace Operations Command and Control (C2) Platform. Its positioning is as the "brain" and "nervous system" of the national cyber defense system. It must achieve a leap from "seeing and seeing clearly" to "being able to analyze, decide, and command," and ultimately bridge the gap between daily security operations and wartime emergency command.
8.2. Core Functional System
The functional design of an advanced command platform should be closely built around the golden rule of combat decision-making—the OODA Loop (Observe-Orient-Decide-Act).
- Panoramic Situational Awareness (Observe)
- Multi-Source Data Fusion: Aggregates multi-dimensional, heterogeneous data sources from network traffic, endpoint logs, threat intelligence, cloud monitoring, physical security, and more.
- Cyberspace Map: Constructs a nationwide, dynamically updated map of critical information infrastructure assets through active and passive mapping techniques, clearly showing the relationships between assets, businesses, vulnerabilities, and threats.
- Visual Presentation: Presents complex cyber confrontation situations through multi-layered, drill-down visualizations such as geographic information maps, topology diagrams, and attack chain views, providing commanders with an intuitive "battlefield picture."
- Intelligent Decision Support (Orient & Decide)
- Intelligent Analysis and Attribution: Uses artificial intelligence and knowledge graphs to automatically correlate massive, fragmented alerts into complete attack events and quickly trace the source, path, and intent of the attack.
- Impact Assessment and Wargaming: Based on a digital twin environment, quickly assesses the potential impact of an attack on core business operations (e.g., economic loss, scope of service interruption) and simulates the consequences of different response plans (e.g., "pulling the plug," switching to backup systems).
- Intelligent Course of Action Recommendation: Based on a built-in expert knowledge base and attack-defense playbooks, the platform can automatically recommend the optimal operational plans, response procedures, and force compositions to the commander based on the current situation.
- Integrated Command and Dispatch (Act)
- Operational Task Management: Supports commanders in creating, decomposing, distributing, and tracking the status of operational tasks.
- Command Issuance: Provides secure, reliable, multi-channel pathways for issuing commands, ensuring that instructions are accurately transmitted to frontline execution units and personnel.
- Automated Coordinated Response: Deeply integrated with SOAR and other automation platforms, allowing commanders to issue commands with a single click to automatically orchestrate distributed firewalls, EDRs, and other security devices across the country for coordinated blocking and response, achieving "planning in the command tent to defeat the enemy a thousand miles away."
8.3. Key Technology Support
- Big Data Technology: Big data stacks like Hadoop, Spark, and Elasticsearch are fundamental for processing terabytes or even petabytes of security data daily, ensuring the platform's analytical performance.
- Artificial Intelligence and Knowledge Graphs: Machine learning is used for anomaly detection and threat identification; knowledge graphs are used to build "entity-relationship" networks, connecting isolated IPs, domains, samples, vulnerabilities, APT organizations, etc., giving the platform the ability to "think."
- Digital Twin: By creating digital mirrors of critical infrastructure, it provides a risk-free, high-fidelity experimental environment for "pre-war wargaming" and "post-war reviews" of operational plans.
- Secure and Reliable Communications: Adopts national cryptographic algorithms, quantum communication, and other technologies to ensure the absolute security and availability of the command platform itself and its command links during intense confrontations.
8.4. Construction Challenges and Future Directions
Building a national-level cyberspace operations command platform is an extremely complex systems engineering project, facing numerous challenges:
- Heterogeneous Systems and Data Interoperability: Seamlessly integrating thousands of different vendors and models of security devices and IT systems to achieve data unification and interoperability is a huge engineering challenge.
- Human-Machine Collaborative Decision-Making: How to build commander trust in AI-recommended solutions and design a "human-machine collaborative" decision-making mechanism that leverages AI efficiency while incorporating human expert experience and intuition is a core scientific problem.
- Platform Self-Security: As the "brain" of the defense system, the command platform itself will inevitably become a top-priority target for enemy attacks. How to ensure the platform's own autonomy, control, security, and trustworthiness is a top priority in its construction.
The future direction is to build an "intelligent defense brain" with self-learning and self-evolving capabilities, able to continuously learn, adapt, and optimize in a constantly changing battlefield environment like a human commander, ultimately achieving "decision advantage" in cyberspace.
Chapter 9: Strategic Foresight—Building a Future-Oriented National Cybersecurity Defense System
9.1. Core Conclusions and Findings
Through a systematic study of national-level cyberspace security attack-defense exercises, this report draws the following core conclusions:
- The Exercise is the Battlefield, Confrontation is the Norm: National-level attack-defense exercises have transcended traditional training, becoming the "primary battlefield" for great powers to display strength, test rules, and engage in strategic gaming in cyberspace. Their status in the national security system is now equivalent to that of traditional military exercises.
- A Trinity of "Technology-Talent-Mechanism": The success or failure of exercises, and indeed the outcome of cyber warfare, ultimately depends on the combined strength of three core pillars: the advancement and autonomy of technology, the scale, quality, and practical ability of talent, and the collaborative efficiency and decision-making level of the mechanism. These three are mutually reinforcing and indispensable.
- Real-Combat Orientation is the Eternal Pursuit: Judging from real-world conflicts like the Russia-Ukraine war, a gap still exists between current exercises and actual combat. China's exercise system still has significant room for improvement in the realism of scenarios (especially in simulating hybrid and cognitive warfare), the autonomy and control of technology (particularly in core chips, operating systems, and industrial software), the fluidity of cross-departmental collaboration, and the effective transformation of exercise outcomes.
9.2. Policy Recommendations
To build a future-oriented national cybersecurity defense system, this report proposes the following policy recommendations:
- Strengthen Top-Level Strategic Planning: Formulate a "National Cyberspace Security Exercise Mid- to Long-Term Development Strategy (2025-2035)," systematically planning exercises as a core component of the cyber power strategy, and clarifying development goals, key tasks, and resource guarantees.
- Improve the Legal and Regulatory Framework for Exercises: Promote the introduction of "Regulations on the Management of Cybersecurity Attack-Defense Exercises" to provide clear legal authorization and behavioral boundaries for high-intensity, realistic exercises, addressing long-standing "legal risk" concerns and clearing the way for "real-world" confrontations.
- Increase Investment in Core Infrastructure: Establish a national special fund for continuous investment in building next-generation national cyber ranges (digital twin ranges), a national threat intelligence sharing platform, and a cyberspace operations command platform. Promote their opening and sharing with key industries and local governments.
- Prudently Conduct International Cooperation and Exchange: While adhering to the principle of independence and autonomy, maintain an open and cooperative attitude to selectively conduct joint exercises and technical exchanges with friendly nations and international organizations. Actively participate in global cyberspace governance, learn from advanced experiences, and convey China's voice.
9.3. Technology Development Roadmap
- Tackle "Chokepoint" Key Technologies: Establish national major science and technology projects to concentrate efforts on tackling core technologies such as next-generation cyber range engines, automated attack/defense (AI for Attack/Defense), AI security, data security, quantum security, Industrial Control System (ICS) security, and autonomous and controllable digital twins.
- Build a National "Arsenal" and "Ammunition Depot": Establish a state-led, multi-party-built, dynamically updated national vulnerability database, attack signature library (TTPs library), and security knowledge graph. This will serve as the source of high-quality "ammunition" for exercise Red Teams and the foundational dataset for training defense systems and AI models, making it a true national core digital asset.
9.4. New-Type Cybersecurity Talent Cultivation Strategy
- Construct an Integrated Industry-Academia-Research-Application Cultivation Model: Break down the barriers in talent cultivation between universities, research institutes, and enterprises. Encourage top companies and universities to jointly establish "Modern Cybersecurity Industry Colleges," bringing real cases and scenarios from attack-defense exercises into the classroom and promoting project-based learning (PBL) oriented toward practical combat capabilities.
- Establish a National Elite Talent Selection and Reserve Mechanism: Drawing on the "whole-nation system" in sports, explore setting up national cybersecurity "junior classes" and "elite classes" to systematically cultivate talented individuals selected from a young age. Include winners of national-level exercises in a national cybersecurity elite talent reserve, providing special policy support.
- Reform Talent Evaluation and Incentive Systems: Establish a talent evaluation and certification system centered on practical attack-defense capabilities (e.g., national-level Red/Blue Team certifications) and link it to professional titles, salary, and career development. This will completely reverse the evaluation orientation that overemphasizes "papers and certificates" and incentivize more talent to devote themselves to the frontline of practical attack and defense.
9.5. Final Outlook: From "Passive Defense" to "Active Defense" to "Deterrent Defense"
The ultimate goal of cyberspace security is not an "absolute security" that is never breached, but the establishment of a dynamic, resilient deterrent balance that makes adversaries "dare not attack, cannot attack, and will not want to attack." Through continuously deepened, systematically advanced, and combat-driven national-level attack-defense exercises, our country's cybersecurity defense system is bound to achieve a historic strategic leap:
- Passive Defense: Blocking and killing threats based on known vulnerabilities and signatures, always playing catch-up.
- Active Defense: Proactively discovering and eliminating potential threats through threat hunting and attack surface management, keeping the enemy at bay.
- Deterrent Defense: Forming a credible cyber deterrence through the demonstration of strong defensive resilience, precise attribution capabilities, and reliable counter-strike power shown in exercises, thereby fundamentally deterring potential cyberattack attempts.
This is not just a technological evolution but a sublimation of strategic thinking. Ultimately, a powerful exercise system, forged through countless trials, will win strategic initiative for our country in the increasingly fierce great power cyber competition and build an unbreakable digital great wall for the construction of a cyber power and the great rejuvenation of the Chinese nation.
References
This list compiles all web resources, technical documents, and related publications cited during the writing of this research report. To ensure completeness and traceability, the list uniformly organizes the title, source/publisher, and available link for each reference.
- A Detailed Explanation of Defense Planning and Implementation in Cybersecurity Attack-Defense Exercises. Chaitin Rivers. Available at:
https://rivers.chaitin.cn/blog/cqtksqh0lne6bf932pgg - What is the Organizational Structure of a Cybersecurity Attack-Defense Exercise? What are the Defensive Measures? CSDN Blog. Available at:
https://blog.csdn.net/tigerman20201/article/details/127208394 - Cyber Attack-Defense Simulation and Urban Security Drills - A Hightopo Digital Twin Original. CSDN Blog. Available at:
https://blog.csdn.net/HUANGXIN9898/article/details/140689402 - Guo, Suchang et al. A Study on Cybersecurity Digital Twins [J]. Information Security and Communications Privacy. Published via SecRSS. Available at:
https://www.secrss.com/articles/58666 - Trends and Dynamics of U.S. Military Cyber Exercises in 2021. SecRSS. Available at:
https://www.secrss.com/articles/41816 - Enduring Partnerships in Cyberspace. Indo-Pacific Defense FORUM. Available at:
https://ipdefenseforum.com/zh-hant/2024/03/%E7%B6%B2%E8%B7%AF%E7%A9%BA%E9%96%93-%E7%9A%84-%E6%8C%81%E4%B9%85%E5%A4%A5%E4%BC%B4%E9%97%9C%E4%BF%82/ - Threat Intelligence. The DFIR Report. Available at:
https://thedfirreport.com/services/threat-intelligence/ - Sekoia.io Endpoint Agent Documentation. Sekoia.io. Available at:
https://docs.sekoia.io/integration/categories/endpoint/sekoiaio/ - Highlights of NATO's "Locked Shields 2024" Exercise. Xinhua Net. Available at:
http://www.news.cn/mil/2024-05/07/c_1212359470.htm - NATO's Cyber Defense Exercise: Locked Shields. SecRSS. Available at:
https://www.secrss.com/articles/58106 - Mr-xn/RedTeam_BlueTeam_HW: Tools and resources for Red vs. Blue teaming and Hynet exercises. GitHub. Available at:
https://github.com/Mr-xn/RedTeam_BlueTeam_HW - 8.2. Red vs. Blue Confrontation - Web Security Learning Notes. Read the Docs. Available at:
https://websec.readthedocs.io/zh/latest/defense/redteam.html - 2024 Sanzhanggui Book Giveaway Event #14: Cyber Range and Attack-Defense Exercises. CSDN Blog. Available at:
https://blog.csdn.net/CC1991_/article/details/136728371 - Search Results - Chinese Journal Service Platform. CQVIP. Available at:
https://qikan.cqvip.com/Qikan/Search/Index?key=K%3D%E6%8E%A8%E6%BC%94%E7%B3%BB%E7%BB%9F&from=Qikan_Search_JournalSearch - 2024 Annual Development Analysis of U.S. Cyber Warfare Equipment. Tactical Missile Technology / SecRSS. Available at:
https://www.secrss.com/articles/79003 - 2024 Analysis of Progress in Foreign Cyber Exercises. Information Security and Communications Privacy Magazine / SecRSS. Available at:
https://www.secrss.com/articles/77181 - Effectively Defend Our Country's Cyber Sovereignty. Qiushi. Available at:
http://www.qstheory.cn/qshyjx/2024-11/15/c_1130219653.htm - Effectively Defend Our Country's Cyber Sovereignty (Targeted Analysis). People's Daily Online - Theory. Available at:
http://theory.people.com.cn/n1/2024/1115/c40531-40361704.html - Russia's "Internet Disconnection" Drill Aims to Prevent National Cyber Lifeline from Being Controlled by Others, Tests National-Level Intranet. The Paper. Available at:
https://m.thepaper.cn/kuaibao_detail.jsp?contid=5389989&from=kuaibao - Analysis and Reflections on Russia's National "Internet Disconnection" Drill. SecRSS. Available at:
https://www.secrss.com/articles/19862 - Li Xin, People's Public Security University of China: Cyber Attack-Defense Exercises and Their Practical Significance. SecRSS. Available at:
https://www.secrss.com/articles/8366 - Strategic Thinking and Insights on Cyberspace Security. Classified Protection. Available at:
https://www.ahdbcp.com/article/625.html - Promote the Leapfrog Development of the Military's Cyberspace Information System. Qiushi. Available at:
http://www.qstheory.cn/20250608/e49093a53b56436b8df6f67ef2e67dab/c.html - U.S. Military Cyber Attack Force Construction and Training Support. SecRSS. Available at:
https://www.secrss.com/articles/30728 - C2. CYBER RANGES. Available at:
https://cyberranges.com/scenarios/c2/ - Cyber Range platform / Cyber security exercises. Digital Marketplace. Available at:
https://www.applytosupply.digitalmarketplace.service.gov.uk/g-cloud/services/144449126749811 - 8 Common Attack Methods in Attack-Defense Exercises and Their Response Guides. Qingteng Cloud Security. (Link missing or inaccessible)
- Attack-Defense Exercises | Building an All-Scenario Defense System, Yaxin-Sec Enhances Government and Enterprise Security Capabilities. Yaxin-Sec. (Link missing or inaccessible)
- Information Security Framework and Technology for Digital Twin Systems from a Bionic Perspective. Zhejiang University Journal Network. (Link missing or inaccessible)
- Comparison of Sino-U.S. Cybersecurity Attack-Defense Exercises: A Perspective on U.S. Cyber Storm VII. FreeBuf.COM. (Link missing or inaccessible)
- Five Key Highlights of NATO's "Locked Shields" Cybersecurity Exercise. GoUpSec. (Link missing or inaccessible)
- The Scoring Mechanism of NATO's Cyber Defense Exercise (Locked Shields). N/A. (Link missing or inaccessible)
- Observations on NATO's "Crossed Swords" Cyber Exercise. Institute for National Defense and Security Research - Defense Security Biweekly. (Link missing or inaccessible)
- "Red vs. Blue Confrontation Exercise Scoring System" Open Source Framework (Preview). JDArmy Blog. (Link missing or inaccessible)
- [PDF] Beijing Huaru Technology Co., Ltd. 2024 Annual Report Summary. Huaru Technology. (Link missing or inaccessible)
- Search results for "National Security". Commercial Times. (Link missing or inaccessible)
- "National Cyberspace Security Strategy" Released. Cyberspace Administration of China. (Link missing or inaccessible)
- "National Cyberspace Security Strategy" Released, Proposing to Defend Cyberspace Sovereignty. The Central People's Government of the People's Republic of China. (Link missing or inaccessible)
- Full Text of the "National Cyberspace Security Strategy". Cyberspace Administration of China. (Link missing or inaccessible)
- Observations and Reflections on Russia's 2019 Internet Disconnection Test and Cyber Sovereignty Legislation. Sohu. (Link missing or inaccessible)
- An Analysis of the Construction of Russia's National Cyber Range System. Development Research Center of the State Council Database. (Link missing or inaccessible)
- Symbiotic Fusion: A New Form of Joint Operations Command System. China Military Online. (Link missing or inaccessible)
- Promote the Leapfrog Development of the Military's Cyberspace Information System. CCTV.com - Military Channel. (Link missing or inaccessible)
- Luxembourg Cyber Range. N/A. (Link missing or inaccessible)